Oracle SSO, SOS
You've probably seen the news: Oracle Cloud got popped, exposing 6 million records from over 140,000 tenants.
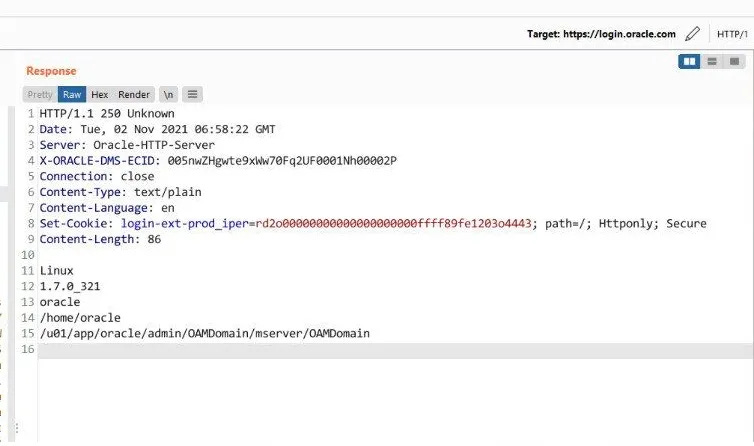
The breach came to light after user "rose87168" dropped the loot on Breach Forums. The alleged attacker disclosed to Bleeping Computer that they used a known vulnerability to hit Oracle Cloud's SSO endpoint at login.<region>.oracle.com.
Chances are, it was either CVE-2021-35587 or CVE-2022-21445. Both issues were discovered and reported by our very own Đức Nguyễn, together with Jang Nguyen, who's also joined our red team on many fun adventures. Duc found the bugs before he even joined the team.
As Duc explained in his blog, these are monster bugs, affecting a wide swath of Oracle products and companies.
During their research, Jang and Duc even managed to pwn multiple systems under oracle.com, including the SSO endpoint at login.oracle.com.
In 2023, we used the same vuln to compromise an Oracle BI instance buried deep inside a bank during a beautiful money heist simulation.
Oracle products are notoriously complex, and Oracle is not exactly famous for fast patching. It took them more than six months to fix CVE-2021-35587 and CVE-2022-21445. Some deprecated product lines never got patches at all. As a result, many Oracle systems are left outdated and vulnerable.
At this point, if you're running Oracle, it's probably safer to assume you're already breached, and plan your defense accordingly.


Good post. We recently posted a report on a connection in the Oracle Cloud-Health breaches and give credit to Duc and Jang, https://medium.com/@hammer_63600/decoding-the-oracle-cloud-health-attack-did-legacy-gateways-expose-medical-records-for-millions-beaa6c9c83e0